What are the types of Wireless Networks?
Wireless data networks exist in such number and variety as to be difficult to categorize and compare.
Some wireless data networks run over wireless voice networks, such as mobile telephone networks. CPDP, HSCSD, PDC-P, and GPRS are examples. Other wireless networks run on their own physical layer networks, utilizing anything from antennas built into handlheld devices to large antennas mounted on towers. 802.11, LMDS, and MMDS are examples. A few wireless networks are intended only to connect small devices over short distances. Bluetooth is an example.
Wireless networks which run over other wireless networks often utilize the lower layer networks to provide security and encryption. Stand-alone wireless networks either provide their own security and encryption features or rely upon VPN's (Virtual Private Networks) to provide those features. In many cases, multiple layers of security and encryption may be desirable.
Some wireless networks are fixed, meaning that antennas do not move frequently. Other wireless networks are mobile, meaning that the antenna can move constantly. This is sometimes a feature of the specific implementation and antenna design, instead of an inherent limitation of the wireless network specification.
Wireless networks may operate on licensed or unlicensed portions of the frequency spectrum.
Common Wireless Network Types
Major types of wireless networks include:
| CDPD | Cellular Digital Packet Data |
| HSCSD | High Speed Circuit Switched Data |
| PDC-P | Packet Data Cellular |
| GPRS | General Packet Radio Service |
| 1xRTT | 1x Radio Transmission Technology |
| Bluetooth |
|
| IrDA |
|
| MMDS | Multichannel Multipoint Distribution Service |
| LMDS | Local Multipoint Distribution Service |
| WiMAX | Worldwide Interoperability for Microwave Access |
| 802.11 | Wi-Fi |
What is Wi-Fi (802.11)?
Wi-Fi (802.11) is a suite of specifications for wireless Ethernet.
802.11 security is a significant concern because 802.11 (Wi-Fi) networks can allow almost untraceable entry into networks.
The 802.11 (Wi-Fi) Standards
The 802.11 standards are defined by the IEEE (Institute of Electrical and Electronic Engineers) at http://grouper.ieee.org/groups/802/11/.
| Standard | Speed | Frequency | Modulation |
|---|---|---|---|
| 802.11 | 2Mb | 2.4GHz | Phase-Shift Keying |
| 802.11a | 54Mb | 5GHz | Orthogonal Frequency Division Multiplexing |
| 802.11b | 11Mb | 2.4GHz | Complementary Code Keying |
| 802.11g | 54Mb | 2.4GHz | Orthogonal Frequency Division Multiplexing |
The 802.11 (Wi-Fi) Channels
The most common 802.11 specification, 802.11b, defines twelve channels. These channels utilize overlapping frequencies. Channels one, six, and eleven do not overlap.
| Channel | US Frequency | European Frequency | Japanese Frequency |
|---|---|---|---|
| 1 | 2412 |
|
|
| 2 | 2417 |
|
|
| 3 | 2422 | 2422 |
|
| 4 | 2427 | 2427 |
|
| 5 | 2432 | 2432 |
|
| 6 | 2437 | 2437 |
|
| 7 | 2442 | 2442 |
|
| 8 | 2447 | 2447 |
|
| 9 | 2452 | 2452 |
|
| 10 | 2457 | 2457 |
|
| 11 | 2462 | 2462 |
|
| 12 |
|
| 2484 |
What is 802.11a?
802.11a is one of the many standards used for high speed wireless networks, usually referred to as Wifi. This standard was created by the IEEE (Institute of Electrical and Electronics Engineers) in 1999 and uses several different frequencies including 5.15-5.35/5.47-5.725/5.725-5.875 GHz to send and receive data from one electronic or computer device to another. There are many different standards of the 802.11 used today for wireless communication; the other popular standards include 802.11b, 802.11g and 802.11n. The standard 802.11a has been available for several years, but has not caught on and is not used as widely as other standards- specifically 802.11b and "g".
Millions of people each year are adding Wifi networks, either for their home, small business or corporate enterprise. While most home networks and small businesses have not embraced 802.11a, one sector that is more willing to use this standard is corporate enterprises.
802.11a is not very popular among small businesses or home networks, but has become popular among corporate users; here is how this standard stacks up in the attributes that matter. These attributes include Speed, Range, Clarity of the Signal, Price and Compatibility
Speed
The max speed of 802.11a is 54 megabits per second; however it is quite fast at its standard rate which is about 25 mbps. This makes it more than twice as fast as 802.11g and almost 4 times as fast as 802.11b when using it in day to day operations.
Range
802.11a delivers a range of about 33 meters or about 100 feet. This is about a 1/3 less than its cousin 802.11b which delivers a range of about 150 feet. It should be noted that because 802.11a uses much higher frequencies, there is less interference from cordless telephones and microwave ovens. However, higher frequencies have their limitations; they do not penetrate walls and obstacles as good as lower frequencies and they require more energy to power these devices.
Clarity of the Signal
802.11a operates on the frequency 5.15-5.35/5.47-5.725/5.725-5.875 GHz, for the most part, the clarity of the signal is generally good, and you are less likely to experience interference than other types of 802.11 standards.
Price
The Price for 802.11a is more expensive than both 802.11b and "g". While it does offer great speeds, many individuals might not view the speed worthy for its extra cost. However, for business's that need fast, interference free networks, these costs can be rationalized and accepted.
Compatibility
Unfortunately, 802.11a is not compatible with other types of standards. If you are running a network on 802.11a or have a Wifi card that receives 802.11a signals, do not expect this standard to work with others. There are dual band Wifi router and cards that offer both 802.11a and "b", but they are usually very costly.
What is WiMAX?
WiMAX stands for Worldwide Interoperability for Microwave Access.
WiMAX is a broadband wireless point-to-multipoint specification from the IEEE 802.16 working group.
Unlike wireless LAN technologies such as Wi-Fi (802.11), WiMAX is designed to operate as a wireless MAN (Metropolitan Area Network). This places WiMAX in the same class as the earlier 802.16 standards, MMDS and LMDS.
WiMAX Frequencies
WiMAX variants operate both on FCC licensed frequencies and on unlicensed frequencies.
Licensed WiMAX operates in the 10 to 66GHz range; unlicensed WiMAX operates in the 2 to 11Ghz range.
WiMAX Bandwidth and Range
WiMAX has a theoretical maximum bandwidth of 75Mbps. This bandwidth can be achieved using 64QAM 3/4 modulation. 64QAM can only be utilized under optimal transmission conditions. WiMAX supports the use of a wide range of modulation algorithms to enable the most bandwidth to be realized under all conditions.
WiMAX has a theoretical maximum range of 31 miles with a direct line of sight. Near-line-of-sight (NLOS) conditions will seriously limit the potential range.
In addition, some of the frequencies utilized by WiMAX are subject to interference from rainfade. The unlicensed WiMAX frequencies are subject to RF interference from competing technologies and competing WiMAX networks.
WiMAX Specifications
| Fixed/Mobile | Fixed |
| Circuit/Packet: | Packet |
| Max Bandwidth | 70 Mbps |
| Range | 31 miles |
| Frequency | 10-66GHz, 2-11Ghz |
| Host Network | N/A |
| Definer | IEEE (Institute of Electrical and Electronic Engineers) |
| URL | http://grouper.ieee.org/groups/802/16/ |
What is EVDO?
EVDO is an acronym for "Evolution Data Only" or "Evolution Data Optimized" which is a standard for high speed wireless networks used for Broadband Internet connectivity. EVDO enables computer users to have high speed Internet access without the help of a hotspot. Just by inserting an EVDO card into the computer, users get connected to the Internet within seconds and have Net access at DSL-compatible speeds.
While traditional wireless networks assign a dedicated path between the source and destination for the entire duration of the call very similar to fixed-line telephone networks, EVDO transmits several users' data through a single channel using Code Division Multiple Access (CDMA) as well as Time Division Multiple Access (TDMA) to achieve higher throughput and better utilization of network bandwidth.
The standard underwent many revisions denoted as Rev. 0, Rev. A, and Rev. B and so on. Rev. 0 supports forward link speeds up to 2.4 Mbit/s. while Rev. A can go up to 3.1 Mbit/s. EVDO is part of the CDMA2000 family of standards and has been adopted by many service providers offering high speed broadband connectivity for mobile phone users through CDMA networks. It was developed by Qualcomm during the late 90s. Since the standard was a direct evolution from the 1xRTT standard which carried only data, it was initially called Evolution Data only. Later on, since the word 'only' seemed to add a negative connotation to the name, the name was switched to Evolution Data Optimized. Since the new name was more marketable and sounded more hi-tech, it stuck.
EVDO uses the current broadcast frequencies of existing CDMA networks which is a major advantage when compared to competing technologies which often require expensive hardware and software changes or upgrades to the network. Verizon and Sprint are the two major service providers in the US using EVDO. Verizon has implemented Rev. A throughout its network, and Sprint is rapidly catching up. While there is also a large presence of EVDO technology in Korea, it has made relatively no impact in Europe and countries in Asia which predominantly use the W-CDMA standard for high speed data access.
What is a WEP Key Passphrase?
To understand what a WEP key passphrase is, we first need to understand what WEP is. WEP is the Wired Equivalent Privacy portion of IEEE 802.wireless networks. WEP was introduced to provide security to wireless networks in view of their vulnerability to eavesdropping because of their use of radio waves. WEP uses the stream cipher RC4 for confidentiality. A WEP key is therefore a security code that is generated using this protocol. WEP keys allow computers on a network to exchange encoded messages with one another while hiding the contents of the messages from intruders. This key is what is used to connect to your wireless-security-enabled network.
A WEP key passphrase is a sequence of words or ordinary text that can be used to automatically generate a WEP key. They are generally longer and stronger than most passwords and can go from 8 to 63 ASCII characters. You can use uppercase, lowercase, and even numeric characters to form your passphrase. However, this may weaken your key and make it vulnerable to a dictionary attack. To protect from this kind of brute force attack, you can use Wi-Fi Protected Access (WPA) to automatically generate unique keys. WPA generates unique keys by employing the Temporal Key Integrity Protocol (TKIP) along with the network service set identifier (SSID) to generate unique keys for each wireless client.
A WEP key consists of a string of hexadecimal characters, which include the numbers 0-9 and the letters A-F. Each character represents 4 bits of the key.
The length of a WEP key depends on the type of WEP encryption used. The various WEP key lengths are as follows:
- Standard 64-bit WEP uses a 40-bit key
- . WEP 104-bit uses a 128-bit key.
- 152-bit WEP key.
- Preshared 256-bit WEP key
The strength of the protection given by encryption depends on the choice of encryption key.
Some security limitations of WEP include the following:
- The key size, as cracking a longer key will require more packets to be intercepted.
- The possibility of IV collisions and altered packets, which are not helped at all by a longer key.
- WEP uses RC4 to protect the confidentiality of the transmitted data. Because every device on the network uses one key to encrypt every transmitted packet, an eavesdropper could intercept the WEP encryption and find the key.
WPA is more secure and easier to use than WEP. It requires configuring your router with a passphrase that WPA will use to generate a WEP key.
An alternative is to use WEP key generators. There are several such tools available on the Internet. A WEP key generator generates random hexadecimal values from a passphrase value entered.
You can either use your WEP key or a passphrase to connect your router to the network. Most routers provide for this. If your router is set to WEP, then you need to enter your WEP key. If your router is set to WPA, then you need to set the passphrase that you will be using to connect to the network.
How do I Setup a Wireless Network?For those who have been contemplating setting up a wireless network in their home, there are many reasons to consider how a wireless network will benefit you. One reason that many people decide to set up a wireless network is to share an Internet connection. By setting up a wireless network, several family members can be on the Internet at the same time. As well, the use of a wireless network also make it possible to send files between different computers without having to save the information to a diskette or CD-ROM. To begin setting up your wireless network, you will need a few pieces of hardware:
Connect an Ethernet cable between your computer and a LAN port located at the back of your wireless router. Next, attach another cable between the WAN port of your wireless router and the Ethernet port of your broadband modem. After completing this, the next step is to turn on the wireless router and wait for it to initialize. Most wireless routers ship with default configurations that will allow you to connect to the Internet at this time. Check to ensure that you are able to access the Internet from your computer. If you are unable to connect, check to see if the cables are connected correctly. The next step is to configure the wireless router. Configuring your wireless router is not as difficult as it may first appear. This may not be strictly necessary, but may be a very good idea. This configuration can be used to personalize your wireless router, or to secure it from public access. For example, you will most likely want to set the SSID on your wireless router and you will also probably want to configure WEP. The next step is to install the wireless network adapters in each computer. These wireless cards may come in many form factors, including:
If you have a PCI wireless card, you will need to power off your computer, open the case, and install the PCI card in an available PCI expansion slot. If you have a PCMCIA wireless card, you will only need to slide it into a PCMCIA slot on your notebook PC. If you have a USB wireless adapter, you will only have to connect it to a USB port on your computer. Once the card is physically installed, you will need to install the software that came with the card. Follow the instructions in the package to do so. You will then configure your computer for the SSID and other wireless configuration information to match the options you chose when you configured your wireless router.
Keyboard ShortcutsWindows system key combinations
Windows program key combinations
Mouse click/keyboard modifier combinations for shell objects
General keyboard-only commands
Shell objects and general folder/Windows Explorer shortcutsFor a selected object:
To copy a filePress and hold down the CTRL key while you drag the file to another folder.To create a shortcutPress and hold down CTRL+SHIFT while you drag a file to the desktop or a folder.General folder/shortcut control
Windows Explorer tree control
Properties control
Accessibility shortcuts
Microsoft Natural Keyboard keys
Microsoft Natural Keyboard with IntelliType software installed
Dialog box keyboard commands
APPLIES TO
Keyboard Shortcuts
Keyboard Shortcuts Instead of MouseMany RSI sufferers report that they feel less pain when typing compared to when mousing. Thus, a desire to avoid mouse as much as possible. Below are some tips from on how to survive in Windows 95 without the mouse. More tips are welcome.
Keyboard instead of mouse -- some tips, for Windows 95by Susan Fulton (New York Times) ALT+ SPACEBAR--opens control menu (like clicking on the symbol in the top
Solid Converter PDF 4.0.560 PDF to WordSolid Converter PDF 4.0.560 PDF to Word
Convert PDF to Word, Excel - Easily Editable Documents!
PDF to Excel Conversion. WYSIWYG Content Extraction. Quality Conversions. PDF Creation. Batch-Process Conversions. Software Requirements Hardware Requirements
 PDF2Word (PDF to Word) software exports the text, images and other contents from any PDF document into MS Word document format (RTF or Word), so you can edit and reuse your PDF content. PDF2Word (PDF to Word) preserves the original PDF text, layout and bitmap images in the generated Word document. PDF2Word (PDF to Word) software is a standalone program and does not require Microsoft Word, Adobe Acrobat, or even Acrobat Reader. Features * Convert PDF files into Microsoft Word documents; * Batch PDF to Word conversion - convert multiple documents at once; * Standalone software, MS Word, Adobe Acrobat and Reader NOT required! * Support Command Line Operation (for manual use or inclusion in scripts); * Support Win98/ME/NT/2000/XP/2003/Vista platforms; * Automatically resize PDF page to fit your required Word page size; * Accurately preserve text, pictures, and layout of the original PDF; * PDF to Word is easy to use; * Support multiple documents conversion (Batch Processing); * Support drag and drop PDF files for conversion; * Support PDF1.6 file format (formerly supported only by Adobe Acrobat 7.0); * Converted files can be automatically loaded immediately after conversion is complete; * Support page range conversion (all, from-to, individual pages); * Support English, French, German, Italian, Chinese Simplified, Chinese Traditional, Czech, Danish, Dutch, Japanese, Korean, Norwegian, Polish, Portuguese, Russian, Spanish, Swedish, etc. languages; * Support deletion of graphics and pictures from the generated Word document; * Support encrypted PDF file conversion; * Five reconstruction modes for PDF to Word conversion; * Convert PDF file to flowing MS Word document without text boxes; Code: http://rapidshare.com/files/113296727/PDF2Word_v3.0.rar Super Bluetooth Hack + Remote ControlSuper Bluetooth Hack v1.08SoftwareSuper Bluetooth Hack v1.08 http://rapidshare.com/files/116996647/Super_Bluetooth_Hack_v1.07.rar Pass:23G 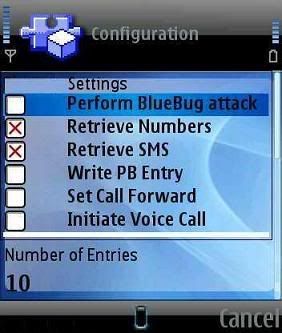 Ultimate Bluetooth Mobile Phone Spy 2008 will work on ALL mobile devices that are bluetooth enabled. Not just phones but also laptops, computers, etc. YOU WILL RECEIVE SEPERATE SOFTWARE FOR OLD MODELS AND NEW MODELS (INCLUDING SYMBIAN PHONES). We don�t need to list compatible phones - this works on ALL phones! Check what your kids, spouse, or partner are up to - and rest at peace! Not just 1 program but an entire suite that will work on old phones, new phones, smart phones, java phones - on absolutely all of them! NOTHING is logged, you leave absolutely NO TRACE of your spying activities! This program is 100% software. You will NOT need to alter or modify your handset at all! 2 extra bonus spy items! * Bluetooth spy suite for your PC/laptop! * A very special program that enables you to view incomming and outgoing e-mail for a given e-mail address. Download:- http://hi5link.com/373/ Bluetooth Remote Control v4.0 Full Retail This is a bluetooth remote controller for PC 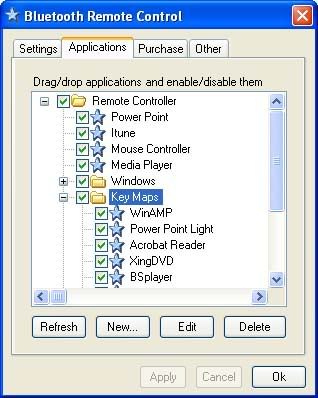 Bluetooth Remote Control turns your Bluetooth enabled mobile phone into a universal controller for Window. See your Power Point slides directly in the phone, browse/play the songs in ITune and Media player and much more... Bluetooth Remote Control is a true universal remote control that lets the user adds or modify the controlled programs. Customize simple keymaps or for full control over the UI write your own Java and VB scripts. Bluetooth Remote Control supports the following programs: Support for additional programs can easily be added with simple keymaps, VB or Java scripts (Script Guide). iTunes � Shows song name, artist & track time and UI objects � Browse playlists, songs, artist, album and composers � Search for songs � Rank tracks � Toggle shuffle � Repeat track or library � Play/pause, rewind, fast forward, change volume, previous/next track � Mute PowerPoint � Shows next slide and slide notes � Shows actual slides � Play/stop presentation, previous/next slide � Load recently used file � Browse/Goto all/any slide � Presentation time � Scroll slide notes � Vibrate when time expires WinAMP � Shows song name, artist & track time and UI objects � Search for song and artists � Play/pause, rewind, fast forward, change volume, previous/next track � Toggle shuffle mode � Change volume � UI objects � Toggle repeat mode Windows Media Player � Shows song name, artist & track time and UI objects � Browse playlists and artists � Rank tracks � Toggle shuffle � Repeat track or library � Play/pause, rewind, fast forward, change volume, previous/next track � Mute Mouse mode � Full support for controlling the PC mouse � See the computer desktop on the phone � Zoom in and out of the desktop � B&W colors for faster response time � Enter text File Browser � Allows launching of files System � Change system volume � Start screensaver � Lock workstation � Shutdown Windows � Start screensaver Here are some key features of "Bluetooth Remote Control": � Control iTunes, PowerPoint, Mouse, WinAMP, Windows Media Player and much more � Create your own applications via Keymaps or VB and JScripts � Supports most Bluetooth enabled phones and all Bluetooth PC solutions � No Bluetooth setup! Just connect from your phone � See the actual desktop in your phone  Download Code: http://rapidshare.com/files/167126879/BTRCv4.rar Mirror Code: http://depositfiles.com/files/qcug0cjma Warelex Mobiola Remote Control 3.0.2 S60v3 (ONLY for Nokia S60 3rd Edition devices) Control your phone via your PC!  Quote: View your phone screen on your desktop PC with Mobiola Remote Phone Control. Take snapshots, record video and share your screen on Skype with this handy app. Enjoy zoom functionality plus Bluetooth compatibility. This is a perfect presentation tool and demo recorder for your Symbian device. * Remotely access and control mobile phone from PC * Control mobile phone with simulation keypad or PC keyboard. * Show screen capture from mobile phone on PC real time * \�zoom in\� and \�zoom out\� and \�full screen\� option * Take screen capture snapshots and real-time video records * Control phone wirelessly over WiFi and Bluetooth or using USB * Demo your phone screen through Skype Video conference and record videos directly to YouTube with webcam driver. Instructions included inside� Download | 6.8 MB: Code: http://rapidshare.com/files/16712821...te_Control.rar Mirror Code: http://depositfiles.com/files/3bhsieysi   This is a easy to use tool manager foe your mobile devices. If you have photos on your phone. This is the tool for you. Send all photos from your phone to the PC easily. You can access your phone to other PC in network and copy needed files, delete not needed photos and so on. This tool allow you to upload any kind of files to your mobile phone in any location. CODE http://kewlshare.com/dl/733ef4e25ed1/Bluetooth_File_Sender_5.rar.htmlSpeedUpMyPC 2009 4.0.2.05SpeedUpMyPC 2009 4.0.2.05 Friday, January 30, 2009CISCO EBOOKS
 Richard Deal, "CCNA Cisco Certified Network Associate Study Guide (Exam 640-802), 3rd edition" McGraw-Hill Osborne Media | ISBN 0071497285 | April 28, 2008 | 983 Pages | PDF | 10.3MB With hundreds of practice questions and hands-on exercises, CCNA Cisco Certified Network Associate Study Guide covers what you need to know-and shows you how to prepare-for this challenging exam. - 100% complete coverage of all official objectives for exam 640-802 - Exam Readiness Checklist at the front and back of the book--you're ready for the exam when all objectives on the list are checked off - Inside the Exam sections in every chapter highlight key exam topics covered - Simulated exam questions match the format, tone, topics, and difficulty of the real exam  Code: http://w16.easy-share.com/1701473699.html Cisco LABS Tutorials (AIO)  Contents:
http://rapidshare.com/files/150917721/cisco_wireless_lans_course.pdf
Latest Wersions of dumps TestInside V3.50  Cisco Certified Network Associate Exam Number/Code: 640-802 Exam Name: Cisco Certified Network Associate Questions and Answers: 183 Q&As Price: $100.00 Update Time: 2008-9-22 TestInside 640-802 Exam Features Quality and Value for the 640-802 Exam TestInside Practice Exams for Cisco 640-802 are written to the highest standards of technical accuracy, using only certified subject matter experts and published authors for development. 100% Guarantee to Pass Your 640-802 Exam If you prepare for the exam using our TestInside testing engine, we guarantee your success in the first attempt. If you do not pass the 640-802 exam (Cisco Certified Network Associate) on your first attempt we will give you a FULL REFUND of your purchasing fee AND send you another same value product for free. Code: http://kewlshare.com/dl/7edb36d396d9/T.I_CCNA_640-802_v3.50.rar.html TestKing V23  Exam Name: Cisco Certified Network Associate Questions and Answers:767 Code: http://kewlshare.com/dl/0d6a443d258d/T.K_CCNA_640-802_V23.rar.html Cisco Packet Tracer 5.0 , Tutorial and ExamplesPacket Tracer 5.0 is the latest version of Cisco Networking Academy’s comprehensive networking technology teaching and learning software. Innovative features of Packet Tracer 5.0, including powerful simulation, visualization, authoring, assessment, and collaboration capabilities, will help students and teachers collaborate, solve problems, and learn concepts in an engaging and dynamic social environment. Packet Tracer makes both teaching and learning easier - instructors and students can create their own virtual “network worlds” for exploration, experimentation, and explanation of networking concepts and technologies. * Instructors can demonstrate technologies and configurations using Packet Tracer to teach complex CCNA-level networking concepts, making it extremely useful for lectures, group and individual labs, assessments, troubleshooting and modeling tasks, homework, games, and competitions. * Students can design, configure and troubleshoot networks using Packet Tracer’s versatile simulation and visualization environment, which also provides the opportunity and flexibility for additional practice outside of the classroom environment. Packet Tracer supplements classroom equipment and provides students complementary learning opportunities that are not physically possible to create in the classroom or lab. In addition, Packet Tracer supplements the CCNA curricula and Packet Tracer activities are integrated throughout both CCNA Discovery and CCNA Exploration to provide rich networking technology learning experiences. Packet Tracer 5.0 offers a unique combination of realistic simulation and visualization experiences, complex assessment and activity authoring capabilities, and opportunities for multiuser collaboration and competition, and is available free of charge to all Networking Academy instructors, students, and alumni. Download: Code: http://rapidshare.com/files/178203604/Cisco.Packet.Tracer.5.0.Tutorial.Examples-WwW.PalDDL.Com.rar Code: WwW.PalDDL.Com CCDP Cisco Internetwork Design Study Guide Code: Download Cisco Router ConfigurationCisco Router Configuration - Interactive Tutorial CCNA1 - Tutorial in HTML file Download Code: http://rapidshare.com/files/165574670/Cd1_Vol-1_Cisco_Router_Configuration.WwW.PalDDL.CoM.rar Code: WwW.PalDDL.CoM CISCO Virtual PC & Laptop BuildingDecember 24th, 2008
System Requirements: Windows 2000/XP, or Vista
Try it Here: Desktop PC Download LINKS ARE INTERCHANGEABLE. IT MEANS YOU CAN DOWNLOAD ANY PART FROM ANY SERVER AND LATER EXTRACT IT. NO PROBLEM AT ALL. Cisco ASA: All-in-One Firewall, Ips, and VPN Adaptive Security Appliance | |||||||||||||||||||||||||||||||
 Back to the top
Back to the top







